Daring to 'Fly Free' with AI Coding, but Also Knowing When to 'Cut Losses' — My Vibe Coding Security Practice Insights
Exploring security considerations for vibe coding from personal experience and reflection, such as risks like key leaks and accidental database deletion, along with practical measures.

Introduction
The first time I tried "vibe coding," it felt like opening a door to a new world. With just one sentence, AI could automatically complete code, realizing all kinds of ideas in my mind. Whether it was a small script or a web service, seeing requirements turn into runnable code was truly addictive. However, gradually, real-world side effects forced me to "pull back." Experiences like leaking keys, accidentally deleting production databases, or bringing test packages into production showed me deeply that: coding with AI is fun and vibe coding is awesome, but if you forget even the most basic security boundaries, it can lead to wasted resources at best, or severe losses at worst.
So how can we enjoy the efficiency and freedom of vibe coding while minimizing security risks? This article summarizes common security blind spots and practical countermeasures in AI-assisted coding based on my personal hands-on "pitfall" experiences, hoping to provide reference and warnings for those eager to try or already deeply practicing vibe coding.
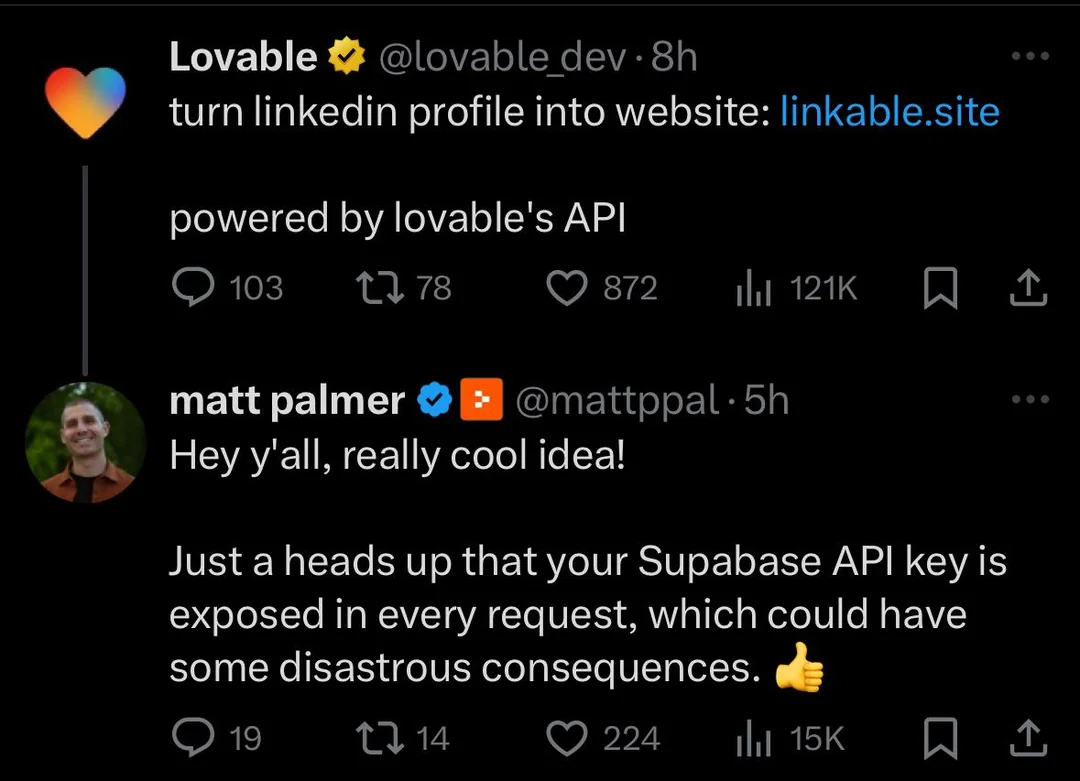
1. How Close Are We to a Security "Short Circuit" with Vibe Coding?
AI-driven vibe coding essentially combines "natural language + auto-completion," emphasizing using intuitive ideas to drive development rhythm, and weakening the traditional process feeling of "design-code-test-launch." This certainly boosts innovation and prototyping power and lowers technical barriers greatly, but precisely because it's so smooth, we subconsciously relax on key security steps—
- Code runs ≠ code is secure. Many AI-generated codes just "make it work" while ignoring basic security measures such as input validation, permission checks, exception handling, and API rate limiting.
- Where you 'don’t understand' is exactly where the biggest risks lie. Often AI assembles functions in a "puzzle piece" style, but as human reviewers, we might miss hidden risks buried in layers of automatic calls, such as direct exposure of sensitive objects, leftover keys, or dependency abuses.
- AI is "too obedient"; if you don’t require security, it won’t add it automatically. For example, many people only say "implement file upload," and LLMs will output workable but dangerous upload interfaces allowing arbitrary file types, path traversal, etc.
- AI is trained in an “insecure” world. The training data for LLMs largely comes from the public internet, where much code is "just a habit" with very low security baselines. If you don't actively demand it, the AI silently reuses these "bad practices" in your projects.
My personal experiences confirm these concerns. For example, once I had AI help build login and payment features, and the code directly placed API keys and database configurations into frontend code. After uploading to GitHub, a security scan alarm went off immediately, causing a cold sweat—if I hadn’t caught it in time, thousands of yuan worth of API calls could have been drained within minutes.
2. Real Cases: You’re Not a True ‘Vibe Coder’ Without Stepping into Some Pits
There’s a saying: AI can make you a “overnight god” or bring you “back to zero overnight.” Here I want to review two typical security pitfalls I personally encountered.
Case 1: Key Leak
I put third-party API keys in .env files and added .gitignore. However, under vibe coding mode, AI automatically wrote env-related config into the code, and after packaging and building, the keys were directly exposed to every user.
Reflection and countermeasures:
- All keys, tokens, and sensitive info must reside only on the server side, managed via environment variables;
.envetc. files must never be pushed to git repos or frontend. - Properly configure
.gitignoreand read-write permissions on critical directories, promote key rotation and regular audits. - Configure ignore files for relevant tools, like
.clineignore. - Use key scanning tools (such as GitGuardian, Snyk, GitHub Secret Scanning) for automatic leak detection.
Case 2: Accidentally Deleting Database — Who Backs Up Your “Rollback”?

Using AI to assist in altering database structure, AI suggested "rebuild table" at deployment, which I blindly agreed to. The test database data was immediately wiped. Although this didn’t affect production, handling test databases this way is troublesome, and worse, if an incompatible AI-generated schema is accidentally executed on the live database, the entire business could crash.
Reflection and countermeasures:
- Strictly separate development, testing, and production environments; hazardous operations like database migration must require multi-level confirmation and trigger automatic backups.
- All automated modification processes must include approvals and “cool-down periods” in CI/CD.
- Business operations must have clear rollback mechanisms with regular drills; all environments should have scheduled automatic backups.
3. How to Build a Security “Gatekeeper” under Vibe Coding?
After many personal lessons, I gradually built a security system suited to vibe coding’s practical environment. The following principles and practical suggestions are results of my ongoing balancing act between aggressive innovation and sober reflection:
A. Security Awareness Is Your First Line of Defense
No matter how "smart" AI is, always assume its output code is “potentially risky.” Before every deployment, I audit from a security perspective as if I were a hacker:
- Use all automated tools like SAST, dependency checks, secret scanning (Snyk, SonarQube, Checkmarx, Dependabot) to review code.
- Code reviews must not be skipped or hurried: carefully review line by line, especially AI-generated parts and bulk changes. Cultivate the habit: AI writes code, but humans make the final call!
- Test cases must cover edge cases including abnormal, malicious input and permission boundaries — not just the AI-generated happy path.
B. Foolproofing Configurations and Standards to Reduce AI Pitfall Space
Many security accidents come from carelessness, not malice. Minimize impact through processes and norms:
- Ensure
.env, configs, database contents, and other sensitive items are ignored and protected before every git commit. - Manage all environments’ sensitive data centrally via environment variables, Secrets Vault, etc., completely forbidding hardcoding.
- Properly configure API and database access permissions, following principle of least privilege and layered authorization—the smaller the privilege, the safer.
- Use “rule files” (like Cursor’s rules, Copilot’s custom instructions) to set AI security baselines such as banning eval, dangerous IO, unverified parameter passing.
C. Clear “Negotiation” with AI — Secure Prompts
AI “only does what you ask,” so explicit secure prompts are crucial. For example:
- “Implement a secure file upload interface allowing only image formats, max 5MB, with randomized filenames stored in a secure directory.”
- “Add authentication, permission checks, and reasonable rate-limiting to all API endpoints.”
- “Check the following code for input validation, SQL injection/XSS issues and fix if any.”
(It’s also recommended for teams to share secure prompt lists to reduce blind spots.)
D. CI/CD Security Processes and Operations Monitoring Must Not Be Absent
Automated scanning and monitoring are your second line of defense to avoid disasters and aid recovery:
- Automatically run security linters, dependency checks, and secret scanning before every merge or release.
- Automate rollback/disaster recovery mechanisms; strictly separate “pre-release,” “production,” and “sensitive operation” permissions.
- Enforce logging in production environments; centralized logs and alert systems can detect abnormal traffic and abuse immediately.
E. Recoverability Is Confidence in Security: Version Control and Code Rollback
Vibe coding with its rapid pace and iterations makes it easy to accidentally break code, data, or dependencies. From practice:
- Version control (e.g., git) must be unconditional, with timely, small commits.
- Critical changes must have undo or snapshot mechanisms; code pushes and rollbacks should be institutionalized.
- Use “approval mode” for AI tools (Cursor, Goose, etc.) to exclude risky automatic bulk source code overwrites.
4. My “Vibe Coding Security Checklist”

Here is my “personal security checklist” for reference, contributions welcome:
- Key/Sensitive Data Management: Store all keys in
.envand backend only, never frontend or repos; conduct regular checks and rotations. - Automated Security Checks: Configure SAST, dependency, and secret scanning tools; enforce CI checks.
- Input/Parameter Validation: All user inputs must be validated and sanitized; backend must not be lax.
- Authentication and Permission Boundaries: Hide API endpoints by default, enforce token validation, ensure users can only perform authorized actions.
- Rate Limiting and Anti-Brute Force: Apply limits to all accounts and important APIs to prevent DoS, burp, brute force attacks.
- Logging and Backup: Log operations, exceptions, and alerts; regularly backup critical data.
- Code Version Management: Normalize git use, small increments, recoverable at every step.
- Production Environment Isolation: Manage by environment, alert on dangerous operations, require multi-level approval.
- Secure Prompts and Rule Files: Prioritize security during AI collaboration with explicit reminders.
- Regular Security Audits: Monthly manual or automated comprehensive code and dependency reviews.
Conclusion
Vibe coding is not a catastrophe; AI assistant’s “dumb” autocomplete and addictive efficiency have raised our development capabilities. But security and responsibility are foundational, never to be dropped. Every pit we fell into, every moment of panic, nourishes the transformation into a mature “security engineer.” When dancing with AI, dare to unleash creativity but also dare to cut losses anytime, guarding the last line.
Let’s embrace vibe coding’s transformation and benefits with safer practices and more responsible mindsets. Keep it up, AI developers who value both security and innovation!
FAQ
Q1: Is AI-written code really secure?
No. AI only produces seemingly usable code based on prompts and training data but won’t automatically add security unless clearly asked. Unreviewed automatic deployment is very risky.
Q2: How to prevent key leakage?
Store all keys and secrets only on backend environment variables, secret managers, etc.; never in code, frontend, repos, or public directories. Regularly check commits and rotate keys.
Q3: What experience is there to prevent “accidental database deletion”?
Don’t include sensitive operations in automated workflows; enforce multi-level approval and auto-backups before all database migrations/deletions; ensure physical separation of production and development/testing environments.
Q4: How to get AI to focus on security during coding?
Explicitly require “security,” “anti-injection,” “valid input,” “rate limiting,” and “code review” in prompts; or declare security requirements centrally in AI tool-supported rule files or custom prompt sets.
Related Resources
- Vibe Coding Security Top 10 | Vibe Security
- Secure Vibe Coding Guide | CSA
- Security in Vibe Coding: The most common vulnerabilities and how to avoid them - ZeroPath Blog
- Secure Vibe Coding: The Complete New Guide - The Hacker News
- Rules Files for Safer Vibe Coding - Wiz Blog
- Fundamentals of web security for vibe coding - cased.com
- Vibe coding service Replit deleted user’s production database, faked data, told fibs galore - The Register
- Security Checklist and Prompt For Vibe Coders
- Securing AI-Driven Vibe Coding in Production - Ardor Cloud



